Many profitable phishing assaults end in a monetary loss or malware an infection. However falling for some phishing scams, like…
Read More

Many profitable phishing assaults end in a monetary loss or malware an infection. However falling for some phishing scams, like…
Read More
Shed a tear, when you can, for the poor, misunderstood cybercriminals exhausting at work attempting to earn a dishonest crust…
Read More
Apr 24, 2025Ravie LakshmananEndpoint Safety / Linux Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a…
Read More
The larger query for a CISO to contemplate, he added, is whether or not information sharing with a 3rd occasion…
Read More
Considered one of your Tesla’s most handy options is its accessibility by means of the Tesla app. From accessing your…
Read More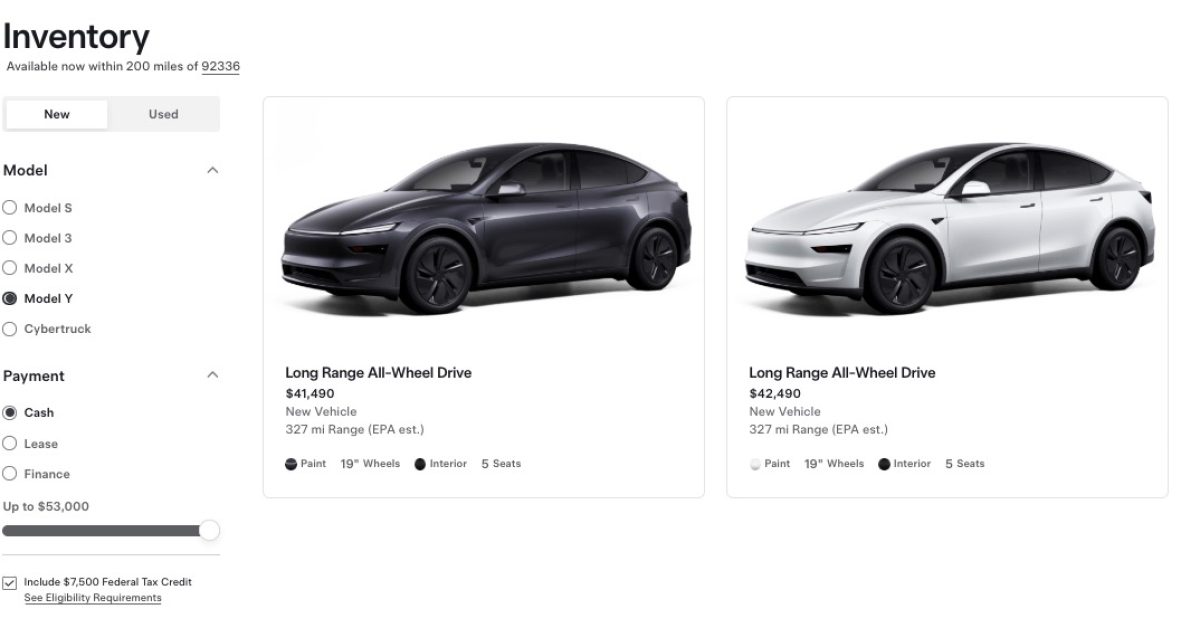
Screenshot Tesla is beginning to replenish its Mannequin Y stock within the US after the design changeover, and it’s ramping…
Read More
Kia has introduced that house owners of the EV6, EV9, and Niro EVs have formally gained entry to over 21,500…
Read More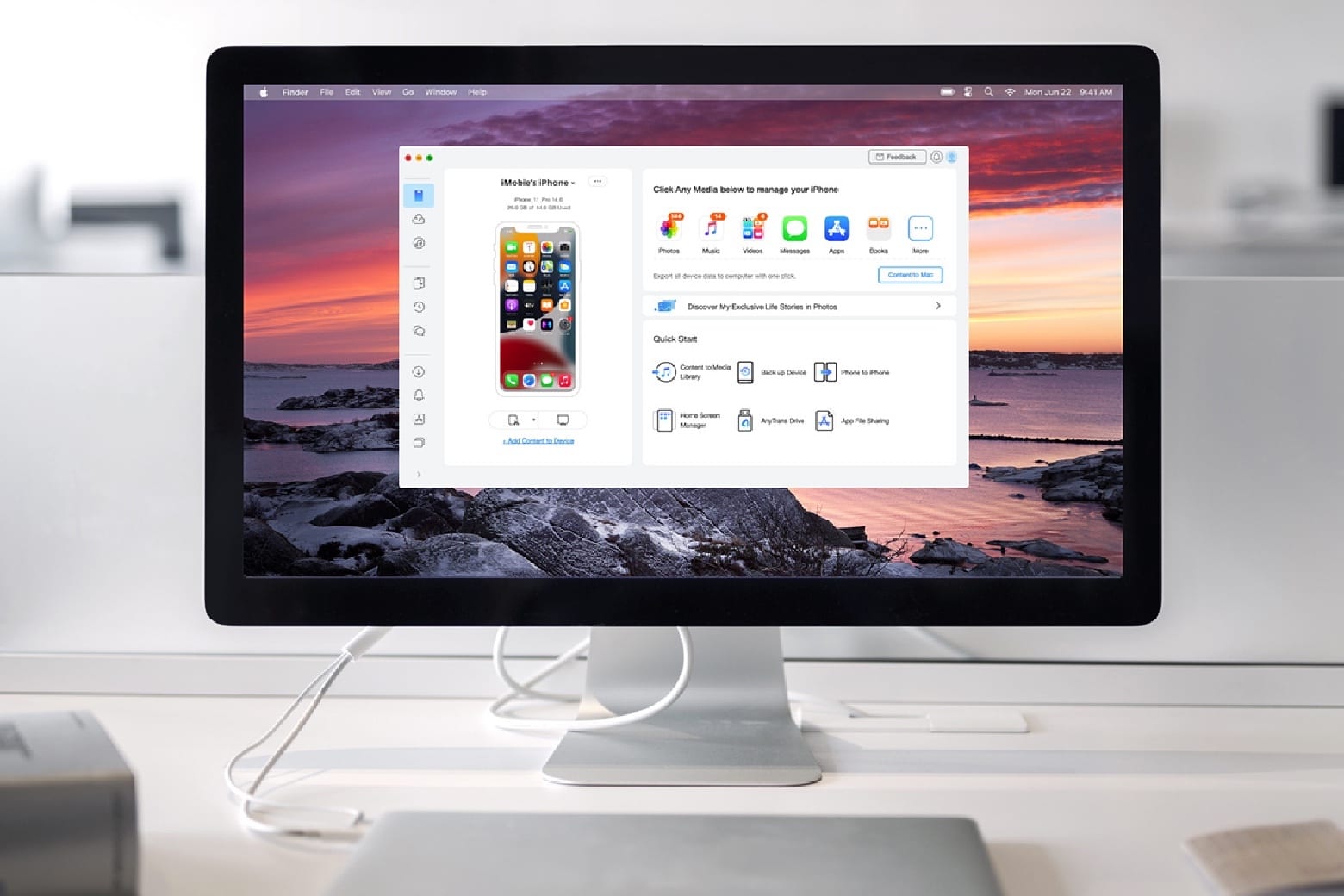
AnyTrans is a one-stop content material supervisor for iOS units. The Mac app makes it straightforward to switch any sort…
Read More
March 25, 2025 PRESS RELEASE Apple’s Worldwide Builders Convention returns the week of June 9 WWDC25 will probably be out…
Read More
On Friday, amid a tariff-induced frenzy that drove hordes of customers to panic-buy iPhones, President Trump introduced a tariff exemption…
Read More