Cybersecurity researchers have found over a dozen safety vulnerabilities impacting Tridium’s Niagara Framework that would enable an attacker on the identical community to compromise the system beneath sure circumstances.
“These vulnerabilities are absolutely exploitable if a Niagara system is misconfigured, thereby disabling encryption on a particular community machine,” Nozomi Networks Labs stated in a report revealed final week. “If chained collectively, they may enable an attacker with entry to the identical community — resembling by means of a Man-in-the-Center (MiTM) place — to compromise the Niagara system.”
Developed by Tridium, an unbiased enterprise entity of Honeywell, the Niagara Framework is a vendor-neutral platform used to handle and management a variety of gadgets from totally different producers, resembling HVAC, lighting, power administration, and safety, making it a useful answer in constructing administration, industrial automation, and good infrastructure environments.
It consists of two key elements: Platform, which is the underlying software program setting that gives the required companies to create, handle, and run Stations, and Station, which communicates with and controls linked gadgets and techniques.
The vulnerabilities recognized by Nozomi Networks are exploitable ought to a Niagara system be misconfigured, inflicting encryption to be disabled on a community machine and opening the door to lateral motion and broader operational disruptions, impacting security, productiveness, and repair continuity.
Probably the most extreme of the problems are listed beneath –
- CVE-2025-3936 (CVSS rating: 9.8) – Incorrect Permission Project for Important Useful resource
- CVE-2025-3937 (CVSS rating: 9.8) – Use of Password Hash With Inadequate Computational Effort
- CVE-2025-3938 (CVSS rating: 9.8) – Lacking Cryptographic Step
- CVE-2025-3941 (CVSS rating: 9.8) – Improper Dealing with of Home windows: DATA Alternate Information Stream
- CVE-2025-3944 (CVSS rating: 9.8) – Incorrect Permission Project for Important Useful resource
- CVE-2025-3945 (CVSS rating: 9.8) – Improper Neutralization of Argument Delimiters in a Command
- CVE-2025-3943 (CVSS rating: 7.3) – Use of GET Request Methodology With Delicate Question Strings
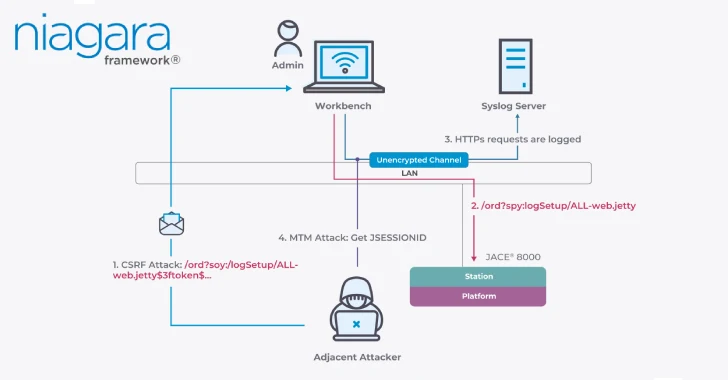
Nozomi Networks stated it was capable of craft an exploit chain combining CVE-2025-3943 and CVE-2025-3944 that would allow an adjoining attacker with entry to the community to breach a Niagara-based goal machine, finally facilitating root-level distant code execution.
Particularly, the attacker may weaponize CVE-2025-3943 to intercept the anti-CSRF (cross-site request forgery) refresh token in eventualities the place the Syslog service is enabled, inflicting the logs containing the token to be transmitted probably over an unencrypted channel.
Armed with the token, the risk actor can set off a CSRF assault and lure an administrator into visiting a specifically crafted hyperlink that causes the content material of all incoming HTTP requests and responses to be absolutely logged. The attacker then proceeds to extract the administrator’s JSESSIONID session token and use it to hook up with the Niagara Station with full elevated permissions and creates a brand new backdoor administrator person for persistent entry.
Within the subsequent stage of the assault, the executive entry is abused to obtain the non-public key related to the machine’s TLS certificates and conduct adversary-in-the-middle (AitM) assaults by benefiting from the truth that each the Station and Platform share the identical certificates and key infrastructure.
With management of the Platform, the attacker may leverage CVE-2025-3944 to facilitate root-level distant code execution on the machine, attaining full takeover. Following accountable disclosure, the problems have been addressed in Niagara Framework and Enterprise Safety variations 4.14.2u2, 4.15.u1, or 4.10u.11.
“As a result of Niagara usually connects crucial techniques and generally bridges IoT expertise and data expertise (IT) networks, it may signify a high-value goal,” the corporate stated.
“Given the crucial capabilities that may be managed by Niagara-powered techniques, these vulnerabilities might pose a excessive danger to operational resilience and safety offered the occasion has not been configured per Tridium’s hardening pointers and finest practices.”
The disclosure comes as a number of reminiscence corruption flaws have been found within the P-Web C library, an open-source implementation of the PROFINET protocol for IO gadgets, that, if efficiently exploited, may enable unauthenticated attackers with community entry to the focused machine to set off denial-of-service (DoS) situations.
“Virtually talking, exploiting CVE-2025-32399, an attacker can power the CPU operating the P-Web library into an infinite loop, consuming 100% CPU assets,” Nozomi Networks stated. “One other vulnerability, tracked as CVE-2025-32405, permits an attacker to jot down past the boundaries of a connection buffer, corrupting reminiscence and making the machine totally unusable.”
The vulnerabilities have been resolved in model 1.0.2 of the library, which was launched in late April 2025.
In latest months, a number of safety defects have additionally been unearthed in Rockwell Automation PowerMonitor 1000, Bosch Rexroth ctrlX CORE, and Inaba Denki Sangyo’s IB-MCT001 cameras that would end in execution of arbitrary instructions, machine takeover, DoS, data theft, and even remotely entry reside footage for surveillance.
“Profitable exploitation of those vulnerabilities may enable an attacker to acquire the product’s login password, acquire unauthorized entry, tamper with product’s information, and/or modify product settings,” the U.S. Cybersecurity and Infrastructure Safety Company (CISA) stated in an advisory for IB-MCT001 flaws.