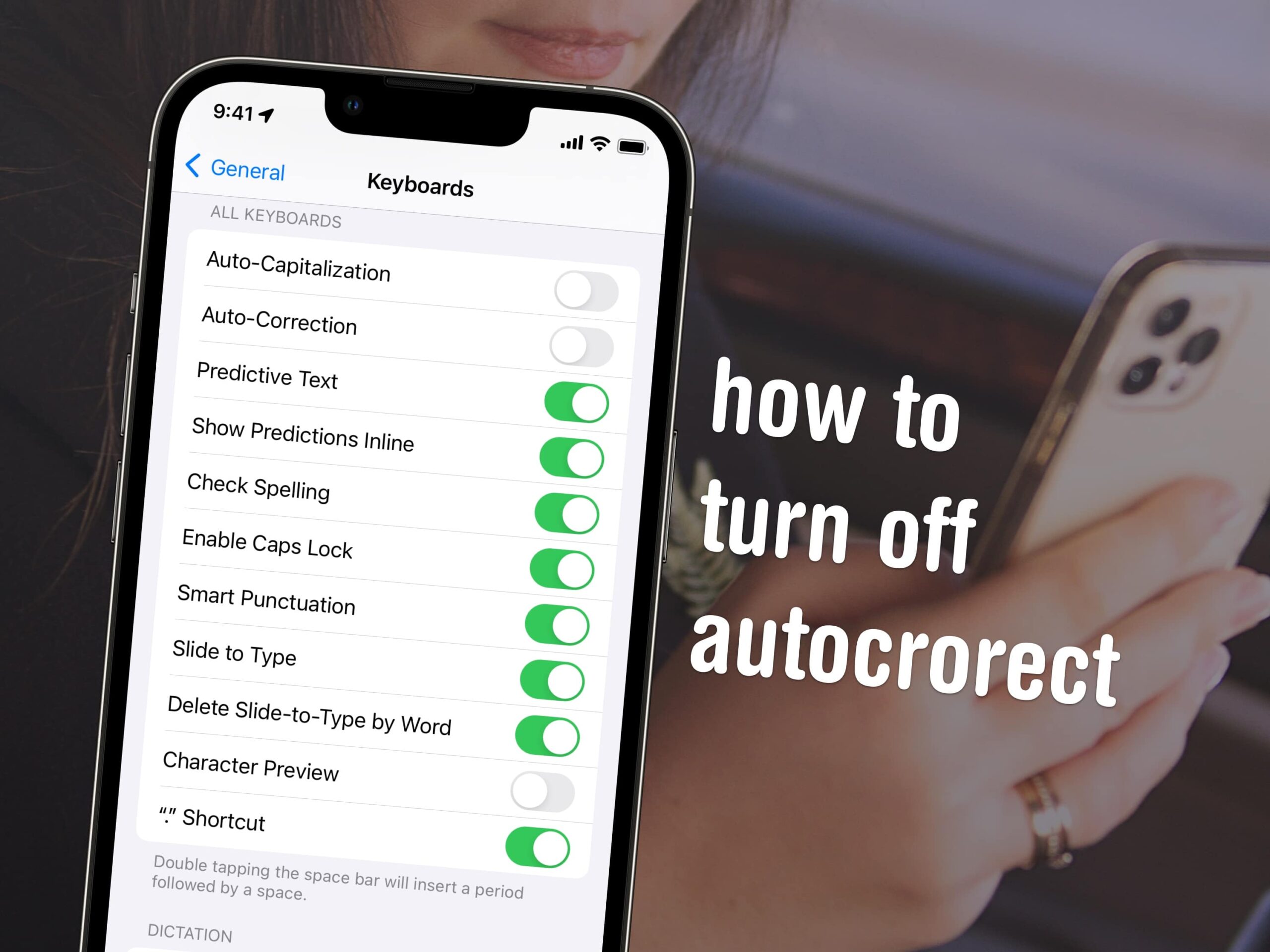
Cybersecurity researchers are calling consideration to phishing campaigns that impersonate fashionable manufacturers and trick targets into calling telephone numbers operated by risk actors.
“A good portion of e mail threats with PDF payloads persuade victims to name adversary-controlled telephone numbers, displaying one other fashionable social engineering method generally known as Phone-Oriented Assault Supply (TOAD), also called callback phishing,” Cisco Talos researcher Omid Mirzaei stated in a report shared with The Hacker Information.
An evaluation of phishing emails with PDF attachments between Could 5 and June 5, 2025, has revealed Microsoft and Docusign to be probably the most impersonated manufacturers. NortonLifeLock, PayPal, and Geek Squad are among the many most impersonated manufacturers in TOAD emails with PDF attachments.
The exercise is a part of wider phishing assaults that try to leverage the belief individuals have with fashionable manufacturers to provoke malicious actions. These messages sometimes incorporate PDF attachments that includes reliable manufacturers like Adobe and Microsoft to scan malicious QR codes that time to faux Microsoft login pages or click on on hyperlinks that redirect customers to phishing pages posing as companies like Dropbox.
QR code phishing emails with PDF payloads have additionally been discovered to leverage PDF annotations to embed the URLs inside a sticky notice, remark, or kind fields inside a PDF attachment, whereas linking the QR codes to an genuine net web page to present the impression that the messages are reliable.
In TOAD-based assaults, victims are coaxed into calling a telephone quantity in a purported try to resolve a problem or verify a transaction. Through the telephone name, the attacker masquerades as a reliable buyer consultant and methods the sufferer into both disclosing delicate info or putting in malware on their units.
Most TOAD campaigns depend on the phantasm of urgency, however their effectiveness typically hinges on how convincingly attackers imitate actual help workflows—utilizing scripted name middle ways, maintain music, and even spoofed caller IDs.
This method has been a fashionable methodology amongst risk actors to put in banking trojans on Android units and distant entry applications on sufferer machines to achieve persistent entry. In Could 2025, the U.S. Federal Bureau of Investigation (FBI) warned of such assaults perpetrated by a financially motivated group referred to as Luna Moth to breach goal networks by posing as IT division personnel.
“Attackers use direct voice communication to use the sufferer’s belief in telephone calls and the notion that telephone communication is a safe solution to work together with a corporation,” Mirzaei stated. “Moreover, the dwell interplay throughout a telephone name permits attackers to control the sufferer’s feelings and responses by using social engineering ways.”
Cisco Talos stated most risk actors use Voice over Web Protocol (VoIP) numbers to stay nameless and make it tougher to hint, with some numbers reused consecutively for as many as 4 days, permitting the attackers to drag off multi-stage social engineering assaults utilizing the identical quantity.
“Model impersonation is among the most fashionable social engineering methods, and it’s repeatedly being utilized by attackers in several types of e mail threats,” the corporate stated. “Subsequently, a model impersonation detection engine performs a pivotal function in defending towards cyber assaults.”
In latest months, phishing campaigns have additionally capitalized on a reliable function in Microsoft 365 (M365) referred to as Direct Ship to spoof inner customers and ship phishing emails with out the necessity for compromising an account. The novel methodology has been employed to focus on greater than 70 organizations since Could 2025, per Varonis.
These spoofed messages not solely appear to originate from contained in the sufferer group, in addition they benefit from the truth that good host addresses observe a predictable sample (“
This tactic shares similarities with vishing, tech help scams, and enterprise e mail compromise (BEC), however differs in supply vector and persistence. Whereas some attackers push victims to obtain distant entry software program like AnyDesk or TeamViewer, others route them via faux cost portals or impersonate billing departments to reap bank card info—broadening the assault floor past simply credential theft.
In a single phishing e mail despatched on June 17, 2025, the message physique resembled a voicemail notification and included a PDF attachment that contained a QR code directing the recipients to a Microsoft 365 credentials harvesting web page.
“In a lot of their preliminary entry makes an attempt, the risk actor utilized M365 Direct Ship performance to focus on a person group with phishing messages that had been topic to much less scrutiny in comparison with customary inbound e mail,” safety researcher Tom Barnea stated. “This simplicity makes Direct Ship a gorgeous and low-effort vector for phishing campaigns.”
The disclosure comes as new analysis from Netcraft discovered that asking massive language fashions (LLMs) the place to log in to 50 totally different manufacturers throughout varied sectors like finance, retail, tech, and utilities recommended unrelated hostnames as responses that weren’t owned by the manufacturers within the first place.
“Two-thirds of the time, the mannequin returned the right URL,” the corporate stated. “However within the remaining third, the outcomes broke down like this: practically 30% of the domains had been unregistered, parked, or in any other case inactive, leaving them open to takeover. One other 5% pointed customers to fully unrelated companies.”
This additionally signifies that customers might be possible despatched to a faux web site simply by asking a synthetic intelligence (AI) chatbot the place to register, opening the door for model impersonation and phishing assaults when risk actors declare management of those unregistered or unrelated domains.
With risk actors already utilizing AI-powered instruments to create phishing pages at scale, the most recent growth marks a brand new twist the place cybercriminals wish to sport an LLM’s response by surfacing malicious URLs as responses to queries.
Netcraft stated it has additionally noticed makes an attempt to poison AI coding assistants like Cursor by publishing faux APIs to GitHub that harbor performance to route transactions on the Solana blockchain to an attacker-controlled pockets.
“The attacker did not simply publish the code,” safety researcher Bilaal Rashid stated. “They launched weblog tutorials, discussion board Q&As, and dozens of GitHub repos to market it. A number of faux GitHub accounts shared a mission referred to as Moonshot-Quantity-Bot, seeded throughout accounts with wealthy bios, profile pictures, social media accounts and credible coding exercise. These weren’t throwaway accounts – they had been crafted to be listed by AI coaching pipelines.”
The developments additionally observe concerted efforts on the a part of risk actors to inject reputed web sites (e.g., .gov or .edu domains) with JavaScript or HTML designed to affect search engines like google into prioritizing phishing websites in search outcomes. That is completed by a bootleg market referred to as Hacklink.
The service “permits cybercriminals to buy entry to hundreds of compromised web sites and inject malicious code designed to control search engine algorithms,” safety researcher Andrew Sebborn stated. “Scammers use Hacklink management panels to insert hyperlinks to phishing or illicit web sites into the supply code of reliable however compromised domains.”
These outbound hyperlinks are related to particular key phrases in order that the hacked web sites are served in search outcomes when customers seek for related phrases. To make issues worse, the actors can alter the textual content that seems within the search outcome to match their wants with out having to take management of the location in query, impacting model integrity and consumer belief.