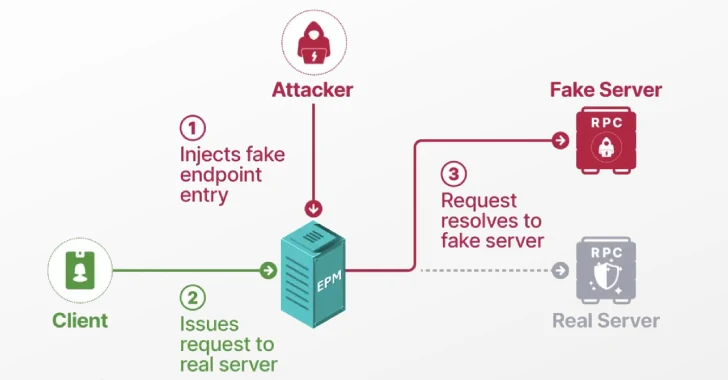
Human identities administration and management is fairly effectively completed with its set of devoted instruments, frameworks, and finest practices. It is a very completely different world relating to Non-human identities additionally known as machine identities. GitGuardian’s end-to-end NHI safety platform is right here to shut the hole.
Enterprises are Shedding Observe of Their Machine Identities
Machine identities–service accounts, API keys, bots, automation, and workload identities–that now outnumber people by as much as 100:1 are in reality an enormous blind spot in corporations’ safety panorama:
With out strong governance, NHIs change into a first-rate goal for attackers. Orphaned credentials, over-privileged accounts, and “zombie” secrets and techniques are proliferating—particularly as organizations speed up cloud adoption, combine AI-powered brokers, and automate their infrastructure.
Secrets and techniques Sprawl: The New Assault Floor
GitGuardian’s analysis reveals that 70% of legitimate secrets and techniques detected in public repositories in 2022 remained energetic in 2025—a three-year window of vulnerability. These aren’t simply theoretical dangers. Breaches at organizations just like the U.S. Division of the Treasury, Toyota, and The New York Occasions all started with a leaked or unmanaged machine id.
The issue is not nearly quantity. Secrets and techniques and credentials are scattered throughout code, CI/CD pipelines, cloud environments, and ticketing programs— environments outdoors conventional safety perimeters.
This proliferation of unmanaged secrets and techniques has caught the eye of safety frameworks worldwide. The newly launched OWASP Prime 10 Non-Human Identification Dangers for 2025 particularly calls out ‘Secret Leakage’ because the #2 threat, noting that compromised credentials are implicated in over 80% of breaches.
Why Secrets and techniques Managers Alone Aren’t Sufficient
Conventional secrets and techniques managers (like HashiCorp Vault, CyberArk, AWS Secrets and techniques Supervisor, and Azure Key Vault) are important for safe storage—however they do not deal with the total lifecycle of NHI governance. They cannot uncover secrets and techniques outdoors the vault, lack context round permissions, and do not automate remediation when secrets and techniques are leaked or misused.
GitGuardian’s personal evaluation discovered that organizations utilizing secrets and techniques managers are in reality extra vulnerable to secrets and techniques leakage. The secrets and techniques leakage incidence of repositories leveraging secrets and techniques managers is 5.1% in contrast with 4.6% for public repositories with out secrets and techniques managers in place. And so as to add so far, repositories with secret managers usually tend to deal with delicate info, growing the chance of publicity.
The Platform Filling the NHI Safety Hole
To handle these challenges, organizations should undertake a unified IAM technique that
empowers DevOps and SRE groups to successfully govern and safe NHIs, on high of the deployment of secrets and techniques administration options (vaults and or secrets and techniques managers). This requires investing in options that present complete secrets and techniques discovery, centralized visibility, and automatic governance capabilities. By leveraging instruments that may map relationships between secrets and techniques, implement constant insurance policies, and streamline rotation and remediation processes, DevOps and SRE groups can scale back the burden of secrets and techniques lifecycle administration and give attention to delivering worth to the enterprise.
GitGuardian’s NHI Safety Platform is designed to deal with these actual blind spots and dangers. Here is how:
1. Discovery and Stock: Discovering the Invisible
Handbook discovery of machine identities is a misplaced battle. Secrets and techniques exist throughout repositories, CI/CD pipelines, ticketing programs, messengers, and cloud environments—usually in locations safety groups do not monitor. Conventional approaches cannot hold tempo with the dynamic nature of contemporary infrastructure, resulting in incomplete inventories.
GitGuardian’s automated discovery repeatedly scans these environments, sustaining a real-time stock enriched with contextual metadata. This centralized view serves as the muse for efficient governance.
2. Onboarding and Provisioning: Securing from Day One
Inconsistent provisioning processes create instant dangers—misconfigurations, over-permissioned identities, and guide errors. Organizations want standardized workflows that implement the least privilege entry and combine with centralized secrets and techniques administration.
A unified platform ensures consistency throughout groups and gives real-time visibility into permissions, sustaining a safe and compliant ecosystem from the beginning.
3. Steady Monitoring: Staying Forward of Threats
Fashionable enterprises face a monitoring nightmare: machine identities work together throughout dozens of programs, every with separate logging mechanisms. With organizations averaging six completely different secret administration situations (in keeping with “Voice of Practitioners: The State of Secrets and techniques in AppSec”), sustaining constant insurance policies turns into practically unimaginable.
GitGuardian aggregates and normalizes utilization information from a number of sources, offering centralized visibility. Superior analytics and anomaly detection allow speedy response to high-risk occasions and coverage violations.
4. Rotation and Remediation: Protecting Credentials Recent
The stakes are excessive: CyberArk studies that 72% of organizations skilled certificate-related outages previously 12 months, with 34% struggling a number of incidents. Managing rotation at scale is complicated, particularly with system dependencies and inconsistent schedules.
GitGuardian integrates with common secrets and techniques managers, offering contextual insights to establish homeowners and streamline remediation, minimizing safety incident influence.
5. Decommissioning: Eliminating Zombie Credentials
Unused or stale identities accumulate as “zombie” credentials—prime targets for attackers. Fragmented tooling and inconsistent processes make correct offboarding troublesome, resulting in persistent safety gaps.
GitGuardian’s steady monitoring identifies candidates for decommissioning.
See GitGuardian’s NHI Safety Platform in motion with our interactive demo. Uncover key options that safety groups and IAM leaders love ⬇️
Compliance and Zero Belief: A Fashionable Mandate
Frameworks like PCI DSS 4.0 and NIST now explicitly demand sturdy controls for machine identities—implementing least privilege, safe onboarding, and steady monitoring. GitGuardian’s platform is constructed with these necessities in thoughts, serving to organizations keep compliant as rules evolve.
Conclusion: Do not Look ahead to a Breach
The stakes are excessive: monetary loss, reputational harm, compliance failure, and—most critically—lack of management over the digital infrastructure that powers your online business.
Ahead-thinking CISOs are bringing NHIs into their IAM technique now. GitGuardian’s platform is the great, automated answer for locating, managing, and securing all of your machine identities—earlier than attackers do.
Be part of us on June 25 for a 20-minute dwell demo of GitGuardian NHI Safety to see how GitGuardian may also help you:
- Get visibility over all NHI secrets and techniques throughout your infrastructure
- Enhance your safety hygiene
- Scale back breaches ensuing from mismanaged identities