Jul 20, 2025Ravie LakshmananDevOps / Menace Intelligence Cybersecurity researchers have alerted to a provide chain assault that has focused standard…
Read More

Jul 20, 2025Ravie LakshmananDevOps / Menace Intelligence Cybersecurity researchers have alerted to a provide chain assault that has focused standard…
Read More
Jul 20, 2025Ravie LakshmananDevOps / Menace Intelligence Cybersecurity researchers have alerted to a provide chain assault that has focused widespread…
Read More
However LAMEHUG’s creators have taken a unique method by constructing the flexibility to question LLMs straight into the malware program…
Read More
Jul 18, 2025Ravie LakshmananCyber Assault / Malware The Pc Emergency Response Group of Ukraine (CERT-UA) has disclosed particulars of a…
Read More
Jul 17, 2025Ravie LakshmananMalware / Social Engineering Risk actors are leveraging public GitHub repositories to host malicious payloads and distribute…
Read More
Jul 16, 2025Ravie LakshmananRisk Intelligence / Vulnerability Cybersecurity researchers have flagged a brand new variant of a identified malware loader…
Read More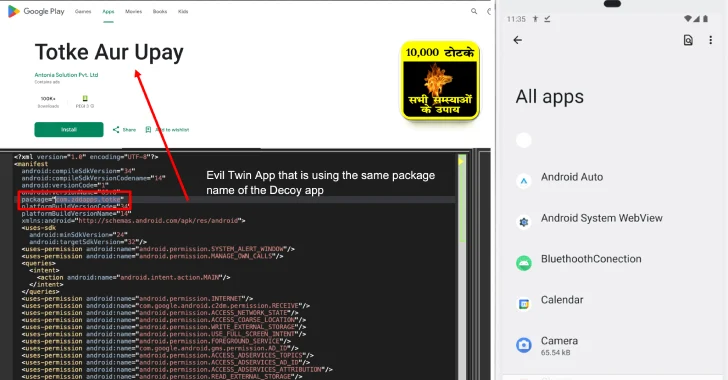
Cybersecurity researchers have found a brand new, refined variant of a identified Android malware known as Konfety that leverages the…
Read More
Cybersecurity researchers have charted the evolution of a broadly used distant entry trojan known as AsyncRAT, which was first launched…
Read More
Jul 15, 2025Ravie LakshmananCyber Espionage / Risk Intelligence Governmental organizations in Southeast Asia are the goal of a brand new…
Read More
Jul 15, 2025Ravie LakshmananMalware / Internet Safety The North Korean risk actors linked to the Contagious Interview marketing campaign have…
Read More