Himaja Motheram, a safety researcher at risk intelligence agency Censys, added: “Whereas attackers do exploit conventional software program flaws, the…
Read More

Himaja Motheram, a safety researcher at risk intelligence agency Censys, added: “Whereas attackers do exploit conventional software program flaws, the…
Read More
A bunch of adults stormed a highschool in Riverside this week and attacked a pupil to hold out revenge for…
Read More
Girls stroll previous a broken home in Bandipora, India, on April 27. Following the April 22 assault that killed at…
Read More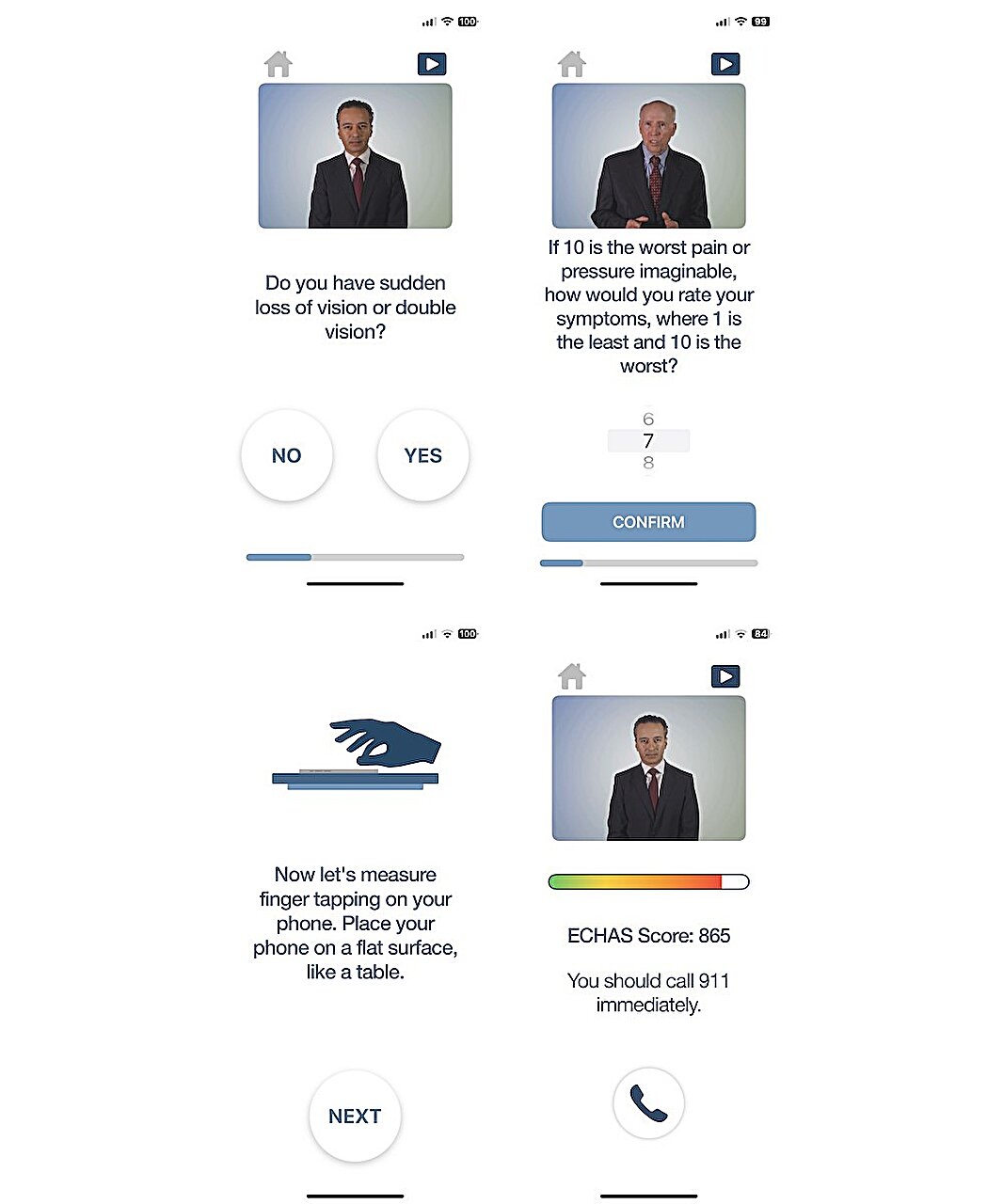
Screenshots of ECHAS (Emergency Name for Coronary heart Assault and Stroke) together with stroke query, myocardial infarction query, finger-tapping, and…
Read More
Might 21, 2025Ravie LakshmananCellular Safety / Browser Safety Cybersecurity researchers have found a brand new marketing campaign that employs malicious…
Read More
Two folks had been fatally shot close to the FBI’s Washington Discipline workplace on Wednesday night time. The deadly capturing…
Read More
Some related attributes on a dMSA account are msDS-DelegatedMSAState, which signifies whether or not the migration course of is unknown,…
Read More
Chris Brown arrived in Manchester on a non-public flight final week, solely to finish up in handcuffs and behind bars.…
Read More
Jason Soroko of Sectigo known as it a “textbook id assault.” “By turning a trusted password protected right into a…
Read More
Unlock the Editor’s Digest totally free Roula Khalaf, Editor of the FT, selects her favorite tales on this weekly publication.…
Read More