Risk actors behind the Interlock ransomware group have unleashed a brand new PHP variant of its bespoke distant entry trojan (RAT) as a part of a widespread marketing campaign utilizing a variant of ClickFix known as FileFix.
“Since Could 2025, exercise associated to the Interlock RAT has been noticed in reference to the LandUpdate808 (aka KongTuke) web-inject menace clusters,” The DFIR Report stated in a technical evaluation printed at present in collaboration with Proofpoint.
“The marketing campaign begins with compromised web sites injected with a single-line script hidden within the web page’s HTML, usually unbeknownst to web site homeowners or guests.”
The JavaScript code acts as a site visitors distribution system (TDS), utilizing IP filtering methods to redirect customers to faux CAPTCHA verification pages that leverage ClickFix to entice them into working a PowerShell script that results in the deployment of NodeSnake (aka Interlock RAT).
The usage of NodeSnake by Interlock was beforehand documented by Quorum Cyber as a part of cyber assaults concentrating on native authorities and better schooling organizations in the UK in January and March 2025. The malware facilitates persistent entry, system reconnaissance, and distant command execution capabilities.
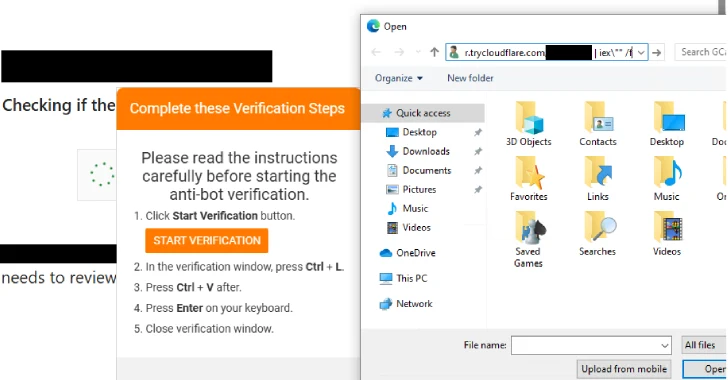
Whereas the title of the malware is a reference to its Node.js foundations, new campaigns noticed final month have led to the distribution of a PHP variant by means FileFix. The exercise is assessed to be opportunistic in nature, aiming for a broad vary of industries.
“This up to date supply mechanism has been noticed deploying the PHP variant of the Interlock RAT, which in sure circumstances has then led to the deployment of the Node.js variant of the Interlock RAT,” the researchers stated.
FileFix is an evolution of ClickFix that takes benefit of the Home windows working system’s capability to instruct victims into copying and executing instructions utilizing the File Explorer’s handle bar function. It was first detailed as a proof-of-concept (PoC) final month by safety researcher mrd0x.
As soon as put in, the RAT malware carries out reconnaissance of the contaminated host and exfiltrate system data in JSON format. It additionally checks its personal privileges to find out if it is being run as USER, ADMIN, or SYSTEM, and establishes contact with a distant server to obtain and run EXE or DLL payloads.
Persistence on the machine is completed by way of Home windows Registry modifications, whereas the Distant Desktop Protocol (RDP) is used to allow lateral motion.
A noteworthy function of the trojan is its abuse of Cloudflare Tunnel subdomains to obscure the true location of the command-and-control (C2) server. The malware additional embeds hard-coded IP addresses as a fallback mechanism in order to make sure that the communication stays intact even when the Cloudflare Tunnel is taken down.
“This discovery highlights the continued evolution of the Interlock group’s tooling and their operational sophistication,” the researchers stated. “Whereas the Node.js variant of Interlock RAT was recognized for its use of Node.js, this variant leverages PHP, a typical internet scripting language, to achieve and preserve entry to sufferer networks.”