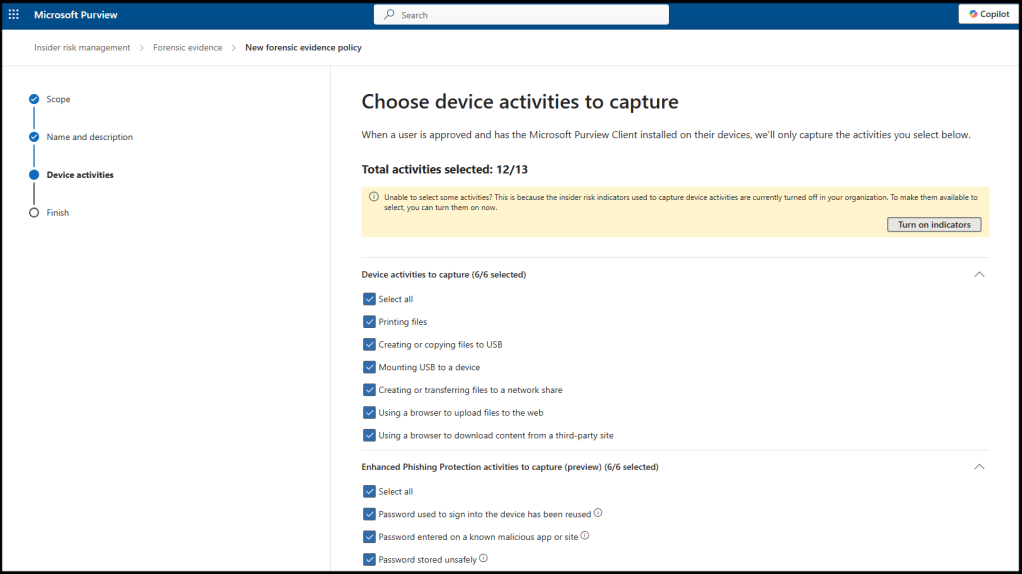
Subsequent you have to create your forensic proof insurance policies. Within the Purview portal, go to “Forensic proof insurance policies” and choose “Create forensic proof coverage.” Specify which actions to seize, equivalent to printing, file exfiltration, particular apps or web sites, or all actions for chosen customers. “All actions” is just not a typical setting and is used just for a set interval throughout an investigation. You may as well use Microsoft 365 Defender’s Superior Looking and Exercise Log options for added forensic evaluation.
Susan Bradley / CSO
Caveats and limitations
Even with these settings, there could be occasions that you’re on the mercy of the seller. Forensic examinations of cloud property could be sophisticated. Monitoring by means of your log recordsdata to assessment what OAuth authentication was abused usually takes skilled assessment of those log recordsdata. In extra you don’t get reminiscence dumps or full management such as you do on endpoints. You usually should open a assist ticket together with your vendor to request log recordsdata, thereby delaying your investigation and response.
There are additionally finances limitations to concentrate on. For instance, it’s possible you’ll must buy extra storage to retailer the forensic proof you want to seize.