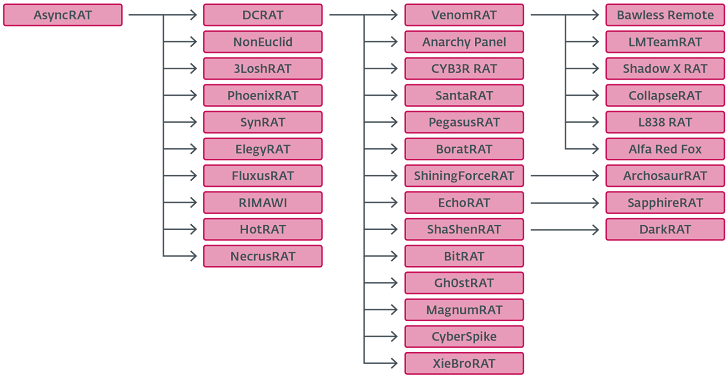
Cybersecurity researchers have charted the evolution of a broadly used distant entry trojan known as AsyncRAT, which was first launched on GitHub in January 2019 and has since served as the muse for a number of different variants.
“AsyncRAT has cemented its place as a cornerstone of recent malware and as a pervasive risk that has advanced right into a sprawling community of forks and variants,” ESET researcher Nikola Knežević mentioned in a report shared with The Hacker Information.
“Whereas its capabilities should not that spectacular on their very own, it’s the open-source nature of AsyncRAT that has really amplified its impression. Its plug-in-based structure and ease of modification have sparked the proliferation of many forks, pushing the boundaries even additional”
Whereas AsyncRAT’s evolution highlights its technical adaptability, its real-world impression stems from the way it’s deployed in opportunistic phishing campaigns and bundled with loaders like GuLoader or SmokeLoader. These supply strategies allow speedy distribution by cracked software program, malicious adverts, or faux updates — concentrating on customers in each company and client environments. With out early detection, AsyncRAT usually acts as a software for info theft and distant management.
First printed on GitHub by NYAN CAT, the C#-based malware is supplied to seize screenshots, log keystrokes, steal credentials, and permit attackers to commandeer contaminated techniques stealthily, exfiltrate information, and execute malicious directions.
The modular software’s simplicity and open-source nature, coupled with its modular structure and enhanced stealth options, has not solely made it very adaptable and more durable to detect, but additionally a beautiful choice for risk actors, as evidenced by the myriad campaigns distributing the risk through the years.
The Slovak cybersecurity firm mentioned the “groundwork” for AsyncRAT was laid earlier by one other open-source RAT often known as Quasar RAT (aka CinaRAT or Yggdrasil) that has been accessible on GitHub since 2015. Though each the malware strains are coded in C#, the wide-ranging variations between them recommend that AsyncRAT was rather more than a fork: It was a serious rewrite.
The 2 items of malware are united by means of the identical customized cryptography courses used to decrypt the malware configuration settings. For the reason that launch of AsyncRAT, the malware has spawned numerous variants, together with DCRat (aka DarkCrystal RAT) and Venom RAT.
DCRat marks a major enchancment over AsyncRAT, packing in evasion strategies to fly underneath the radar and augmenting its capabilities to assemble webcam information, microphone recordings, and Discord tokens, alongside even a module to encrypt recordsdata.
“DCRat additionally implements evasion strategies like AMSI and ETW patching, which work by disabling safety features that detect and log malicious habits,” ESET mentioned. “Addi5onally, it options an anti-process system whereby processes whose names match these in a denylist are terminated.”
Venom RAT, alternatively, is alleged to have been impressed by DCRat, whereas additionally packing in sufficient distinctive options of its personal.
“Whereas they certainly belong to the Quasar RAT household, they’re nonetheless totally different RATs,” Rapid7 researcher Anna Širokova famous in an evaluation of AsyncRAT and Venom RAT in November 2024. “Venom RAT presents extra superior evasion strategies, making it a extra refined risk.”
ESET mentioned it additionally recognized lesser-known variants of AsyncRAT, reminiscent of NonEuclid RAT, which includes plugins to brute-force SSH and FTP credentials, accumulate geolocation, act as a clipper by substituting clipboard information with the attacker’s cryptocurrency pockets addresses, and even unfold the malware by compromising transportable executable recordsdata with an arbitrary payload.
JasonRAT, for its half, introduces bespoke adjustments of its personal, reminiscent of the flexibility to focus on techniques primarily based on nation. Likewise, XieBroRAT incorporates a browser credential stealer and a plugin to work together with Cobalt Strike servers through a reverse connection. It is also tailored for the Chinese language market.
“AsyncRAT’s rise and its subsequent forks spotlight the inherent dangers of open-source malware frameworks,” ESET mentioned. “All of those forks not solely lengthen AsyncRAT’s technical capabilities but additionally reveal how shortly and creatively risk actors can adapt and repurpose open-source code.”
“The widespread availability of such frameworks considerably lowers the barrier to entry for aspiring cybercriminals, enabling even novices to deploy refined malware with minimal effort. This democratization of malware growth – particularly contemplating the rising reputation of LLMs and potential to misuse their capabilities – additional accelerates the creation and customization of malicious instruments, contributing to a quickly increasing and more and more advanced risk panorama.”
This shift has additionally fueled the rise of malware-as-a-service (MaaS), the place preconfigured AsyncRAT builders and plug-and-play modules are bought brazenly on Telegram and darkish net boards. The rising overlap between open-source malware, penetration testing instruments, and business distant entry frameworks complicates attribution and protection.
For safety groups, this implies larger give attention to behavioral detection, command-and-control (C2) evaluation, and understanding how fileless persistence, clipboard hijacking, and credential theft converge in fashionable malware campaigns.