Disclaimer: The content material introduced on this article relies completely on publicly obtainable, unclassified info and open-source analysis. It doesn’t draw upon any categorised or proprietary information. The evaluation is meant solely as a technical thought train to discover potential cybersecurity concerns within the context of legacy plane techniques and industrial management system analogies. This text additionally doesn’t signify official coverage, steerage or suggestions of any authorities or company, neither is it meant to tell acquisition, safety coverage or nationwide protection decision-making. All opinions expressed are these of the creator in a private capability.
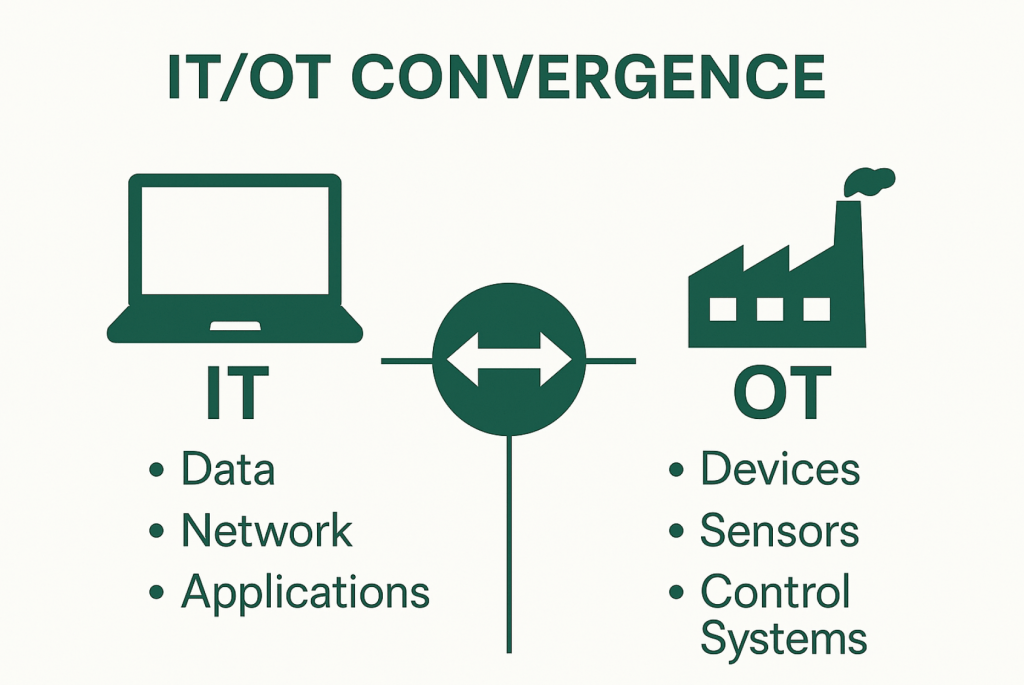
I lately attended an Industrial Management System (ICS) Cybersecurity convention, the place we discovered how one can use info expertise (IT) cybersecurity methods and instruments to deal with operational expertise (OT) safety. It dawned on me that the essential design of plane management techniques is just like the OT techniques we simply discovered about.
Cybersecurity professionals are more and more requested to safe techniques by no means designed for contemporary threats. Impressed by information of the US authorities evaluating a foreign-donated Boeing 747-8 to be used as Air Pressure One (AF1), I felt the retrofit of a legacy plane for nationwide safety use affords a novel lens into the IT/OT convergence drawback, and why bodily entry and legacy protocols should now be handled as front-line dangers.
Daniel Hoffman
Legacy plane, fashionable danger
Whereas the 747-8 is a technological leap past its predecessor, the 747-400, it nonetheless retains legacy protocols and architectures that introduce danger, particularly when repurposed for top-tier nationwide safety missions. Many of those plane techniques resemble industrial management techniques (ICS), comparable to these utilized in important infrastructure. Like legacy supervisory management and information acquisition (SCADA) techniques, plane avionics usually assume trusted inside communication, a belief mannequin not enough in at the moment’s risk panorama.
In manufacturing facility settings, these techniques have been usually “air-gapped” — they have been remoted from different networks as a line of protection and solely workers have been allowed bodily entry. The plane developed equally. One of many predominant strains of protection was burying the cabling and parts within the fuselage the place unauthorized personnel couldn’t entry them.
Because the aircraft we’re accessing was retrofitted abroad, we should assume that there’s potential for implanted, dormant gadgets or tampering with frequent gadgets.
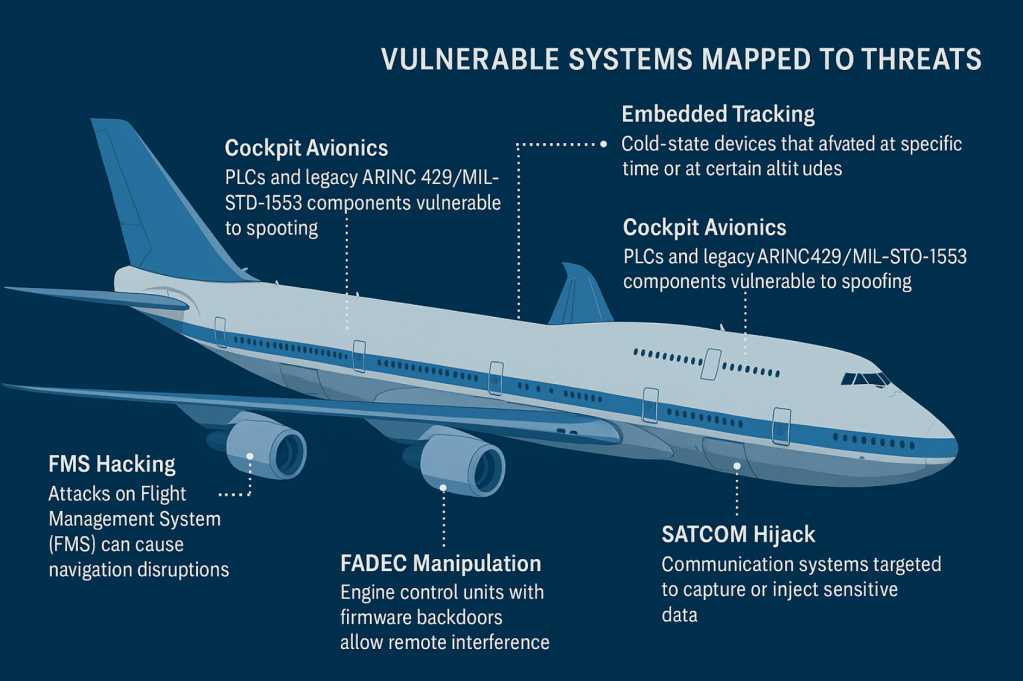
Key vulnerabilities uncovered
| Risk kind | Impression | Activation methodology | Detection methodology |
| {Hardware} implants | Engine/management sabotage | RF set off, preset logic | X-ray, teardown |
| Firmware backdoors | Navigation/system override | GPS/time-triggered code | Reverse engineering |
| Chilly-state trackers | Location exfiltration | Altitude or temp-based | Environmental simulation |
| Radar-based exfiltration | Covert information leaks | Waveform modulation | Anomaly/radar sign evaluation |
| SATCOM hijack | Comms interception | RF sign hijacking | Spectrum monitoring, validation |
| Toolchain exploits | Persistent entry | Malicious diagnostic instruments | Supply and firmware audits |
| MitM on avionics buses | Command injection, replay assaults | Cable tapping/spoofing | Sign integrity/timing evaluation |
| Mobile subsystems | Audio or GPS leakage | Dormant baseband payloads | Spectrum forensics, teardown |
Legacy protocols create new assault surfaces
One of many banes of the OT world is the reliance on legacy expertise that can’t simply be patched or upgraded with out inflicting main disruptions. Equally, the Boeing 747-8 employs a hybrid bus structure. Whereas it integrates fashionable flight administration applied sciences just like the Thales TopFlight Flight Administration System (FMS), many subsystems nonetheless depend on ARINC 429 and MIL-STD-1553, protocols that lack authentication or encryption.
As talked about in arXiv:1707.05032, this may depart vulnerabilities comparable to code injection and manipulation, information injection, information leakage and DoS. Even the newer Ethernet-based techniques utilizing AFDX (ARINC 664) lack cryptographic safeguards. As we simply talked about, historically, the 747 depends on bodily controls comparable to restricted bodily accessibility. On this case, that management has already been compromised.
These channels expose the plane to MitM, spoofing and replay assaults, significantly throughout retrofitting or upkeep cycles. Ukwandu et al. (2022) spotlight the avionics business’s gradual adoption of safe protocols. In industrial management environments, encryption overlays can mitigate comparable threats, however latency considerations make this strategy troublesome to use to real-time flight techniques, the place latency may trigger severe penalties as a consequence of delayed flight management response.
Daniel Hoffman
Implants hidden throughout retrofit
Bodily entry throughout retrofitting introduces different alternatives for adversaries: Embedding covert implants, usually designed to activate underneath particular environmental triggers. Munro (2020) outlines situations the place miniature computer systems (e.g., Raspberry Pi-class) are hid inside avionics bays or energy rails, undetectable with out teardown, sign evaluation or x-ray. These gadgets can be utilized for a wide range of functions.
Implants and embedded surveillance
Surveillance implants will be launched throughout retrofit, as talked about above. Units comparable to passive RF microphones, compromised baseband transceivers or altered inflight leisure techniques could seize delicate audio or telemetry. Habler, Bitton and Shabtai (2022) present how these techniques resist standard detection strategies, making post-deployment audits extraordinarily troublesome. These implants evade customary EM sweeps and require teardown or x-ray inspection for detection.
Surveillance risk vectors
- Passive RF microphones. These gadgets can harvest ambient audio and transmit it utilizing harvested electromagnetic power making them extraordinarily onerous to detect utilizing conventional EM sweeps.
- Compromised baseband transceivers. These are present in satellite tv for pc telephones, LTE modems or embedded SIMs and may silently leak GPS coordinates, conversations or system information.
- Tampered inflight leisure techniques (IFE). IFEs could seem benign however usually sit on segmented but accessible community backplanes. If compromised, they’ll bridge passenger interfaces with avionics.
Non-traditional information exfiltration channels
Relating to information exfiltration in a standard IT/OT setting, we regularly depend on catching them on the best way out by monitoring the transmission strategies. That turns into way more advanced on our 747. Radar emission modulation has been recognized as a viable vector for stealth exfiltration. As outlined in NSA TEMPEST steerage (2023), such strategies mimic regular habits and evade detection. Further pathways embody SATCOM hijacking, Bluetooth beacons or optical LED flicker, all under-monitored in legacy plane. Hardening this aircraft to be used as AF1, we might want to take into account these routes.
The availability chain as a gentle goal
The aviation provide chain continues to current a major cybersecurity danger. Important parts comparable to firmware, diagnostic utilities and upkeep procedures could also be altered or compromised throughout manufacturing or integration, particularly when involving overseas distributors. The danger of malicious implants or latent, persistent vulnerabilities being launched upstream is amplified by restricted provider visibility and inadequate cybersecurity controls throughout tiers (Aerospace Industries Affiliation, 2023).
A extensively cited instance is the 2020 SolarWinds breach, through which attackers compromised the Orion software program replace system to distribute malware to greater than 18,000 organizations, together with US federal companies and Fortune 500 corporations. The incident revealed how deeply embedded vulnerabilities in trusted vendor pipelines can bypass perimeter defenses and persist for months
Inside compromise
Cabin interiors current important dangers, significantly in categorised missions. Seats, partitions and energy shops could conceal passive surveillance gadgets or logic circuits.
To align with SCIF and TEMPEST requirements, finest practices demand:
- Full teardown and rebuild of inside parts
- X-ray and RF scanning of structural cavities
- Chain-of-custody validation for all replacements
- RF shielding and acoustic integrity testing
Requirements like RTCA DO-355, DO-356A and CNSSAM TEMPEST/1-13 are important to assembly government transport and Continuity-of-Authorities mandates, Baker, Arlen & Parkinson, Paul. (2018).
Hardening retrofitted plane: actionable steps
- Apply RTCA and NIST finest practices. Requirements comparable to RTCA DO-355/356A and NIST SP 800-53 provide lifecycle danger frameworks, encryption suggestions and audit mechanisms. Although full-stack encryption could also be infeasible, tailor-made implementations can scale back the assault floor with out compromising efficiency.
- Validate each subsystem. Each avionics and help subsystem should endure teardown, high-resolution imaging and verification towards trusted baselines. Elements failing this scrutiny needs to be changed with licensed home equivalents.
- Safe the toolchain. Distributors should meet DFARS cybersecurity necessities and ideally CMMC Stage 2 or larger. Firmware builders and diagnostic engineers should function inside a verified safe improvement lifecycle (SDLC).
- Implement persistent telemetry and monitoring. Static scans are inadequate. Ongoing community habits evaluation, anomaly detection and forensic auditing are very important. This aligns with DoD suggestions within the 2023 Airborne Programs Value Estimating Information.
Value and acquisition realities
Whereas a donated airframe could seem economical, retrofitting prices can match or exceed new plane procurement. DoD and GAO benchmarks present that safe retrofits could value tons of of thousands and thousands and nonetheless fall wanting purpose-built assurances.
Home management nonetheless issues
Residual danger persists with foreign-origin techniques, even after exhaustive evaluate. This underlines the rationale behind VC-25B (Subsequent AF1) procurement, a platform constructed domestically, underneath safe situations. The mission was slated for completion in 2024, Boeing now estimates 2027 – 2028. Which might nonetheless put supply in keeping with, or forward of a retrofit mission, which may take 2-4 years in accordance with Protection One and Aviation Supply Information.
For a have a look at what would go into attempting to safe this aircraft, learn a pattern blue group playbook.
Conclusion: A playbook for IT/OT convergence
This situation serves as a high-stakes case research in securing legacy, cyber-physical techniques. Cybersecurity leaders will more and more face unconventional challenges. Whether or not it’s an influence plant, a legacy fleet or a retrofitted plane, those that can bridge IT and OT worlds will form the way forward for safety technique.
This text is printed as a part of the Foundry Knowledgeable Contributor Community.
Need to be part of?