Disclosure: Covert Internet-to-App Monitoring through
Localhost on Android
📢 UPDATE: As of June third 7:45 CEST, Meta/Fb Pixel script is not
sending
any packets or requests to localhost. The code accountable for sending the _fbp cookie has been
virtually
fully eliminated.
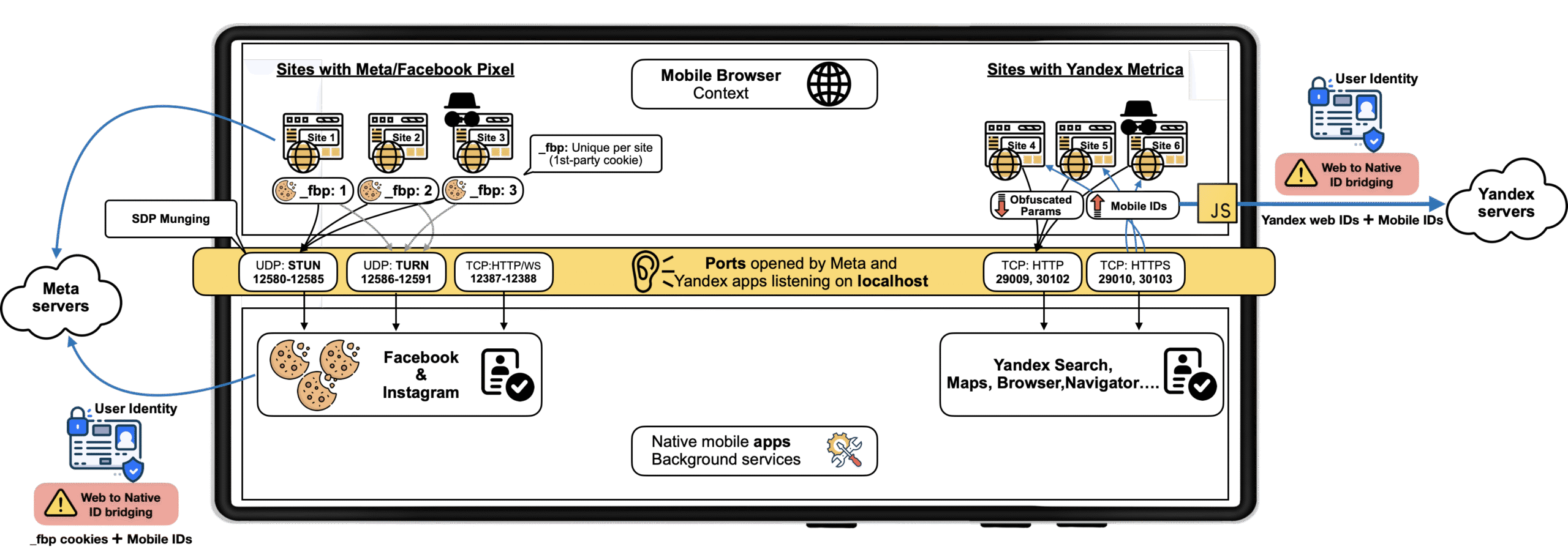
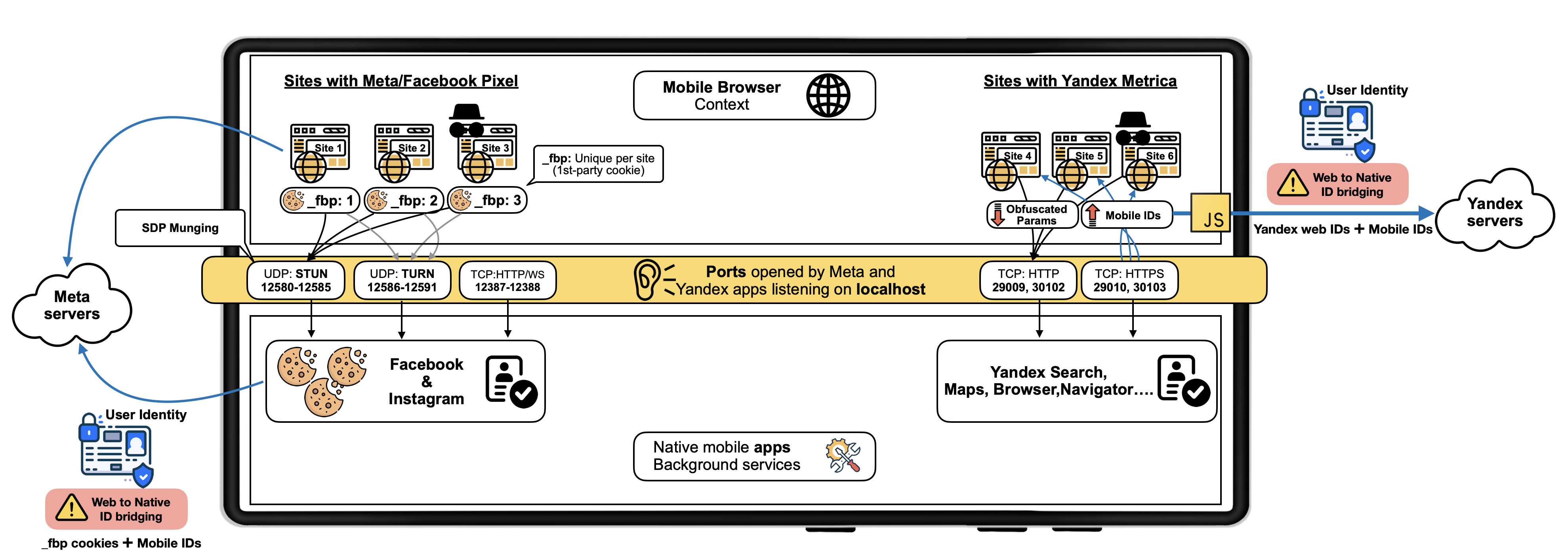
We disclose a novel monitoring technique by Meta and Yandex probably affecting
billions of Android customers. We discovered that native Android apps—together with Fb,
Instagram, and
a number of Yandex apps together with Maps and Browser—silently hear on mounted native
ports for monitoring functions.
These native Android apps obtain browsers’ metadata, cookies and instructions from
the Meta Pixel and Yandex Metrica scripts embedded on hundreds of internet sites. These JavaScripts load
on customers’ cell browsers and silently join with native apps working on the identical system by way of
localhost sockets. As native apps entry programatically
system identifiers just like the Android
Promoting ID (AAID) or deal with person identities as within the case
of Meta apps, this technique successfully permits these organizations to hyperlink cell
shopping classes and net cookies to person identities, therefore de-anonymizing customers’
visiting websites embedding their scripts.
This web-to-app ID sharing technique bypasses typical privateness protections similar to clearing
cookies, Incognito Mode and Android’s permission controls. Worse, it opens the door for probably
malicious apps eavesdropping on customers’ net exercise.
📁 Further Sources
– Video exhibiting Yandex sending localhost requests. The left window exhibits a
distant debugging inspector window of the browser on the Android telephone.
The best window exhibits the display screen of the Android telephone, with our proof-of-concept app on the prime and
the browser on the backside:
– Video exhibiting Meta Pixel sending localhost STUN requests. The left window
exhibits Wireshark, a program that screens net site visitors.
The best window exhibits the browser visiting a web site. Notice that the requests solely begin sending
as soon as the web page is loaded when emulating a Android telephone (Pixel 7)
and the breakpoint added to the Fb script is handed:
– Picture exhibiting Meta Pixel parameters for which ports and protocols to
contact localhost.
![]()
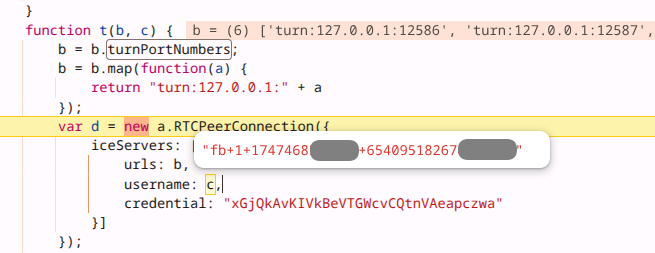
– Picture exhibiting Meta Pixel performing SDP Munging to insert the _fbp cookie
worth.
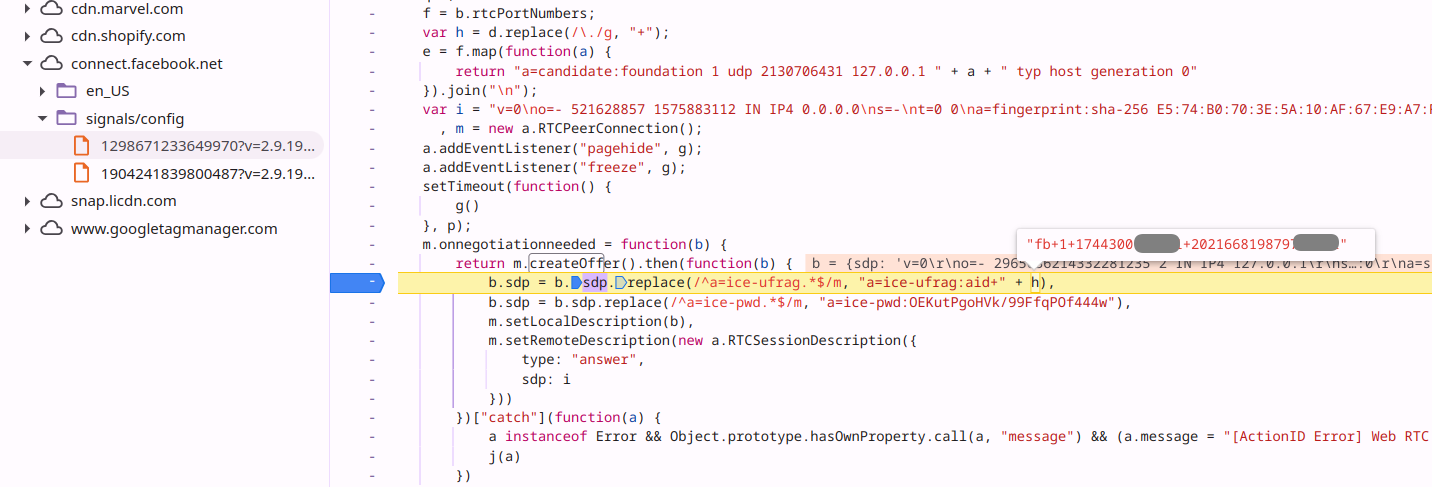
– Picture exhibiting Meta Pixel utilizing STUN to _pass fbp cookie worth to cell
apps.