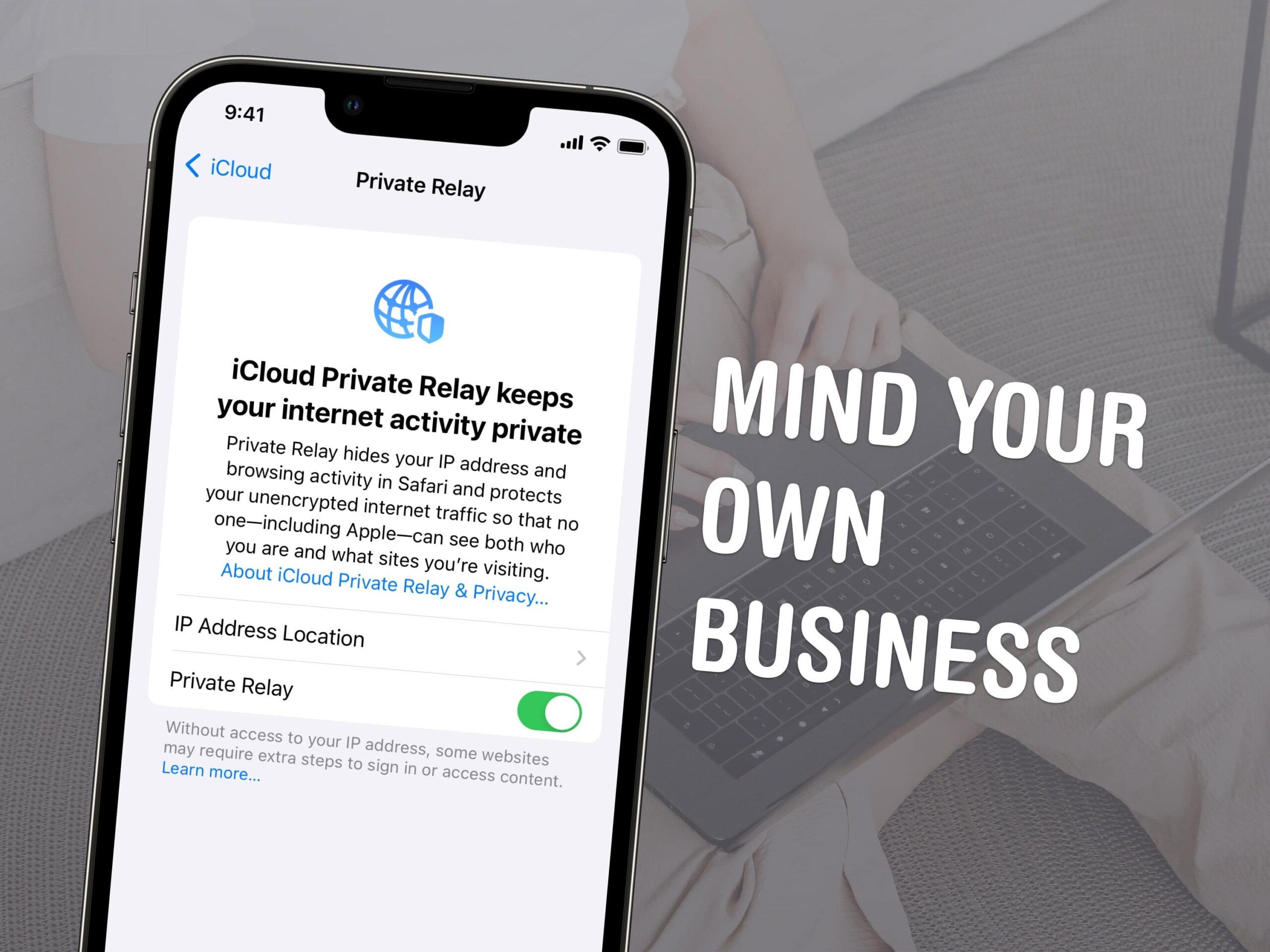
Take, as an example, the infamous Russian state-sponsored group behind the SolarWinds breach. Microsoft calls it Midnight Blizzard, however safety groups would possibly encounter it as Cozy Bear, APT29, NOBELIUM, UNC2452, Darkish Halo, or any of greater than 10 different names throughout numerous safety companies.
“Safety groups usually get a number of alerts about the identical group of attackers, however every alert makes use of a unique identify. This implies they waste time chasing the identical difficulty a number of instances,” Singh defined. “Valuable time wanted to react rapidly to an assault is misplaced whereas groups are busy correlating menace names.”
Kumar Avijit, vp at Everest Group, pointed to cases the place the confusion has actual penalties. “In follow, the coexistence of a number of aliases for a similar adversary has hampered safety groups’ potential to rapidly correlate intelligence feeds, share findings, and prioritize response actions,” Avijit mentioned. “This mismatch can result in duplicated efforts, delaying incident response, and go away gaps in protection when defenders assume they’re monitoring distinct threats.”