Cybersecurity researchers have warned of a brand new spear-phishing marketing campaign that makes use of a respectable distant entry device referred to as Netbird to focus on Chief Monetary Officers (CFOs) and monetary executives at banks, vitality firms, insurers, and funding corporations throughout Europe, Africa, Canada, the Center East, and South Asia.
“In what seems to be a multi-stage phishing operation, the attackers aimed to deploy NetBird, a respectable wireguard-based distant entry device on the sufferer’s pc,” Trellix researcher Srini Seethapathy stated in an evaluation.
The exercise, first detected by the cybersecurity firm in mid-Could 2025, has not been attributed to a identified menace actor or group.
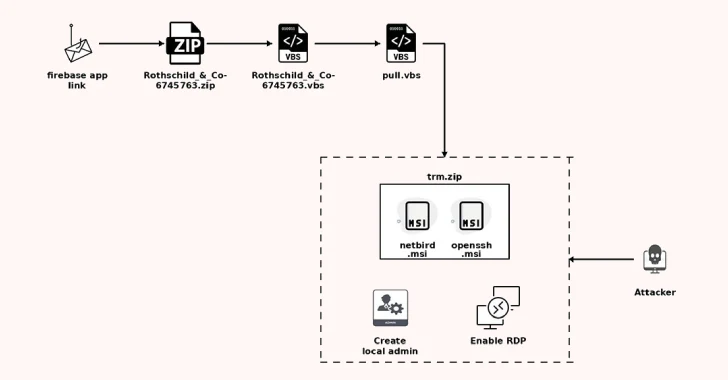
The start line of the assault is a phishing electronic mail that impersonates a recruiter from Rothschild & Co. and claims to supply a “strategic alternative” with the corporate. The e-mail is designed to entice the recipients into opening a purported PDF attachment that, in actuality, is a phishing hyperlink that redirects them to a Firebase app-hosted URL.
What’s notable concerning the an infection is that the actual redirect URL is saved within the web page in encrypted type and is accessible solely after the sufferer solves a CAPTCHA verification test, finally resulting in the obtain of a ZIP archive.
“Fixing the puzzle executes a [JavaScript] perform that decrypts it with a hard-coded key and redirects the person to the decrypted hyperlink,” Seethapathy stated. “Attackers are leaning on these customized CAPTCHA gates an increasing number of, hoping to slide previous defenses that already flag phishing websites protected by Cloudflare Turnstile or Google reCAPTCHA.”
Current inside the archive is a Visible Fundamental Script (VBScript) that is answerable for retrieving a next-stage VBScript from an exterior server and launching it by way of “wscript.exe.” This second-stage VBScript downloader then fetches one other payload from the identical server, renames it to “trm.zip,” and extracts two MSI information from it: NetBird and OpenSSH.
The final section includes putting in the 2 packages on the contaminated host, making a hidden native account, enabling distant desktop entry, and persisting NetBird by way of scheduled duties such that it robotically launches on system reboot. The malware additionally removes any NetBird desktop shortcuts to make sure that the compromise isn’t detected by the sufferer.
Trellix stated it recognized one other redirect URL that has been lively for almost a 12 months and serves the identical VBScript payload, indicating that the marketing campaign might have been round for a while.
The findings as soon as once more present how adversaries are more and more relying on respectable distant entry purposes akin to ConnectWise ScreenConnect, Atera, Splashtop, FleetDeck, and LogMeIn Resolve to ascertain persistence and use it to burrow into the sufferer’s community, whereas concurrently evading detection.
“This assault is not your typical phishing rip-off,” Seethapathy stated. “It is well-crafted, focused, refined, and designed to slide previous know-how and other people. It’s a multi-stage assault the place the adversary makes use of social engineering and protection evasion strategies to create and preserve persistent entry to the sufferer system.”
The disclosure coincides with the invention of varied email-based social engineering campaigns within the wild –
- Assaults that abuse a trusted area related to a widely known Japanese web service supplier (ISP) to ship phishing messages from the e-mail tackle “firm@nifty[.]com” in an try to get previous electronic mail authentication checks and harvest credentials
- Assaults that abuse the Google Apps Script growth platform to host phishing pages that look respectable and steal Microsoft login credentials by using invoice-themed electronic mail lures
- Assaults that mimic an Apple Pay bill to steal delicate person knowledge, together with bank card particulars and Yahoo Mail account particulars
- Assaults that abuse Notion workspaces to host phishing pages that trick customers into clicking on hyperlinks that take the victims to a pretend Microsoft login web page below the guise of viewing a shared doc and exfiltrate the credentials by way of a Telegram bot
- Assaults that exploit a years-old safety flaw in Microsoft Workplace (CVE-2017-11882) to ship the Formbook malware variant hidden in a pretend PNG file and steal delicate knowledge from compromised hosts
PhaaS Providers Decrease the Bar
The findings additionally come as Trustwave detailed the operational connections between Tycoon and DadSec (aka Phoenix) phishing kits, highlighting their infrastructural overlaps and using a centralized phishing infrastructure. DadSec is the work of a menace actor tracked by Microsoft below the moniker Storm-1575.
“The infrastructure utilized by DadSec can be related to a brand new marketing campaign leveraging the ‘Tycoon 2FA’ Phishing-as-a-Service (PhaaS) platform,” Trustwave researchers Cris Tomboc and King Orande stated. “The investigation into the Tycoon2FA phishing package reveals how adversaries proceed to refine and broaden their techniques inside the Phishing-as-a-Service (PhaaS) ecosystem.”
 |
| Tycoon 2FA PhaaS Operation |
The rising recognition of PhaaS providers is evidenced by the emergence of a brand new “plug-and-play” Chinese language-language package dubbed Haozi that is estimated to have facilitated over $280,000 price of felony transactions over the previous 5 months by promoting promoting to third-party providers. It operates on a subscription foundation for $2,000 per 12 months.
“Not like legacy phishing kits that require attackers to configure scripts or infrastructure manually, Haozi provides a glossy, public-facing internet panel,” Netcraft stated. “As soon as an attacker purchases a server and places its credentials into the panel, the phishing software program is robotically arrange, without having to run a single command.”
“This frictionless setup contrasts with different PhaaS instruments just like the AI-enabled Darcula suite, the place minimal command-line utilization continues to be essential.”
Apart from supporting an admin panel the place customers can handle all their campaigns in a single place, Haozi has been discovered to supply promoting area, appearing as an middleman to attach phishing package patrons with third-party providers, akin to these associated to SMS distributors.
 |
| Haozi phishing dashboard |
One other side that units Haozi other than different kits is a devoted after-sales Telegram channel (@yuanbaoaichiyu) to help clients with debugging points and optimizing their campaigns, positioning it as a horny possibility for aspiring cybercriminals who haven’t any technical experience.
“As enterprise safety groups grow to be simpler at detecting and addressing intrusion makes an attempt, attackers are deploying social engineering and phishing scams, techniques that do not require breaching a hardened perimeter,” Netcraft researcher Harry Everett stated.
“PhaaS choices decrease the ability ground and scale campaigns by automation and group assist. These new fashions perform extra like SaaS companies than black-market hacking teams, full with subscription pricing, customer support, and product updates.”
Microsoft, in an advisory revealed final week, revealed how PhaaS platforms are more and more driving adversary-in-the-middle (AiTM) credential phishing because the adoption of multi-factor authentication (MFA) surges.
A few of the different strategies embrace machine code phishing; OAuth consent phishing; the place menace actors make use of the Open Authorization (OAuth) protocol and ship emails with a malicious consent hyperlink for a third-party utility; machine be part of phishing, the place menace actors use a phishing hyperlink to trick targets into authorizing the domain-join of an actor-controlled machine.
The Home windows maker stated it has noticed suspected Russian-linked menace actors using third-party utility messages or emails referencing upcoming assembly invites to ship a malicious hyperlink containing a legitimate authorization code. The method was first documented by Volexity in April 2025.
“Whereas each finish customers and automatic safety measures have grow to be extra succesful at figuring out malicious phishing attachments and hyperlinks, motivated menace actors proceed to depend on exploiting human conduct with convincing lures,” Igor Sakhnov, company vice chairman and deputy CISO of Identification at Microsoft, stated.
“As these assaults hinge on deceiving customers, person coaching and consciousness of generally recognized social engineering strategies are key to defending in opposition to them.”