A China-aligned superior persistent risk (APT) group known as TheWizards has been linked to a lateral motion device known as Spellbinder that may facilitate adversary-in-the-middle (AitM) assaults.
“Spellbinder allows adversary-in-the-middle (AitM) assaults, by IPv6 stateless handle autoconfiguration (SLAAC) spoofing, to maneuver laterally within the compromised community, intercepting packets and redirecting the visitors of reputable Chinese language software program in order that it downloads malicious updates from a server managed by the attackers,” ESET researcher Facundo Muñoz stated in a report shared with The Hacker Information.
The assault paves the best way for a malicious downloader that is delivered by hijacking the software program replace mechanism related to Sogou Pinyin. The downloader then acts as a conduit to drop a modular backdoor codenamed WizardNet.
This isn’t the primary time Chinese language risk actors have abused Sogou Pinyin’s software program replace course of to ship their very own malware. In January 2024, ESET detailed a hacking group known as Blackwood that has deployed an implant named NSPX30 by profiting from the replace mechanism of the Chinese language enter methodology software program utility.
Then earlier this yr, the Slovak cybersecurity firm revealed one other risk cluster often called PlushDaemon that leveraged the identical method to distribute a customized downloader known as LittleDaemon.
TheWizards APT is thought to focus on each people and the playing sectors in Cambodia, Hong Kong, Mainland China, the Philippines, and the United Arab Emirates.
Proof means that the Spellbinder IPv6 AitM device has been put to make use of by the risk actor since not less than 2022. Whereas the precise preliminary entry vector used within the assaults is unknown at this stage, profitable entry is adopted by the supply of a ZIP archive that comprises 4 totally different recordsdata: AVGApplicationFrameHost.exe, wsc.dll, log.dat, and winpcap.exe.
The risk actors then proceed to put in “winpcap.exe” and run “AVGApplicationFrameHost.exe,” the latter of which is abused to sideload the DLL. The DLL file subsequently reads shellcode from “log.dat” and executes it in reminiscence, inflicting Spellbinder to be launched within the course of.
“Spellbinder makes use of the WinPcap library to seize packets and to answer to packets when wanted,” Muñoz defined. “It takes benefit of IPv6’s Community Discovery Protocol through which ICMPv6 Router Commercial (RA) messages promote that an IPv6-capable router is current within the community in order that hosts that help IPv6, or are soliciting an IPv6-capable router, can undertake the promoting machine as their default gateway.”
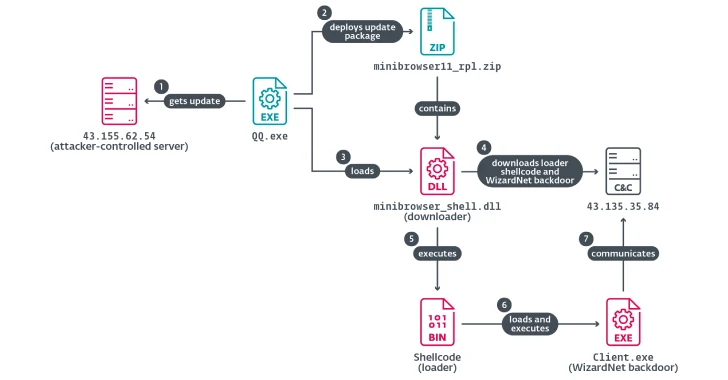
In a single assault case noticed in 2024, the risk actors are stated to have utilized this methodology to hijack the software program replace course of for Tencent QQ on the DNS degree to serve a trojanized model that then deploys WizardNet, a modular backdoor that is outfitted to obtain and run .NET payloads on the contaminated host.
Spellbinder pulls this off by intercepting the DNS question for the software program replace area (“replace.browser.qq[.]com”) and issuing a DNS response with the IP handle of an attacker-controlled server (“43.155.62[.]54”) internet hosting the malicious replace.
One other noteworthy device in TheWizards’ arsenal is DarkNights, which can be known as DarkNimbus by Pattern Micro and has been attributed to a different Chinese language hacking group tracked as Earth Minotaur. That stated, each clusters are being handled as unbiased operators, citing variations in tooling, infrastructure, and focusing on footprints.
It has since emerged {that a} Chinese language public safety ministry contractor named Sichuan Dianke Community Safety Know-how Co., Ltd. (aka UPSEC) is the provider of the DarkNimbus malware.
“Whereas TheWizards makes use of a special backdoor for Home windows (WizardNet), the hijacking server is configured to serve DarkNights to updating functions operating on Android units,” Muñoz stated. “This means that Dianke Community Safety is a digital quartermaster to TheWizards APT group.”